When a DHCP client receives information from a DHCP server only basic information, like IP / subnet / gateway / dns /etc, is visible. In some situations clients also receive DHCP options to set specific settings or application configurations (for example with Microsoft Lync or RES Workspace Manager). Knowing what options are received by the clients helps you troubleshoot.
There are multiple road that lead to Rome, in this article I’ll show you three. For one of them I created a PowerShell script which you can run on any machine.
Three roads to Rome
Although there are probably more, here are three roads that lead to Rome (and with Rome I mean: reading the DHCP options received by the client).
- Wireshark
- DHCP test client
- Windows registry
Wireshark
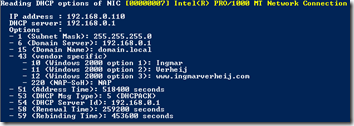
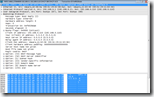 Wireshark gives you (by far) the most detailed information about the DHCP process and information received. Not only does it show you what information is received, it also shows you what packets are send / received over the network.
Wireshark gives you (by far) the most detailed information about the DHCP process and information received. Not only does it show you what information is received, it also shows you what packets are send / received over the network.
![]() All you have to do is install Wireshark on your computer (or run the portable version), start a capture, set the filter to bootp and initiate a DHCP request.
All you have to do is install Wireshark on your computer (or run the portable version), start a capture, set the filter to bootp and initiate a DHCP request.
DHCP test client
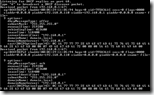 Another great tool to use is the DHCP test client. This sniffs the network until a DHCP Offer / DHCP Ack is detected on UDP port 68 and shows the received information.
Another great tool to use is the DHCP test client. This sniffs the network until a DHCP Offer / DHCP Ack is detected on UDP port 68 and shows the received information.
The benefit of the DHCP test client is that you don’t have to install anything, just run the tool and initiate a DHCP request.
Windows registry
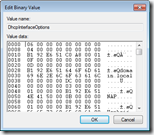 The downside of both Wireshark and the DHCP test tool is that you need to capture the packets from the network when they’re send. Luckily the received packets are stored in the Windows registry key DhcpInterfaceOptions.
The downside of both Wireshark and the DHCP test tool is that you need to capture the packets from the network when they’re send. Luckily the received packets are stored in the Windows registry key DhcpInterfaceOptions.
Unfortunately the content of this key is not easy to read and not documented (?). So without a tool / script the content of this key is useless.
PowerShell script
Since the DhcpInterfaceOptions is always accessible (even when the client already received the DHCP offer) I wanted to have the ability to read the content. So I wrote a PowerShell script that reads the registry key for each DHCP enabled NIC and shows the received DHCP options.
The script shows all Dhcp options and vendor specific Dhcp options (43).
You can find the PowerShell script here: ReadDhcpOptions
The archive contains three files
- DhcpOptions.csv – Semicolon separated file containing all Dhcp Options (IANA) and their data type;
- DhcpOptionsVS.csv – Semicolon separated file containing some vendor specific Dhcp Options;
- ReadDhcpOptions.ps1 – The actual PowerShell script
PS: My PowerShell-force is not strong, yet I managed to show the required data
Reverse engineering
Since the content of the DhcpInterfaceOptions key is not documented (or maybe I’ve searched on the wrong location) I had to reverse engineer the content. Once you know how the data is stored it’s really easy 🙂
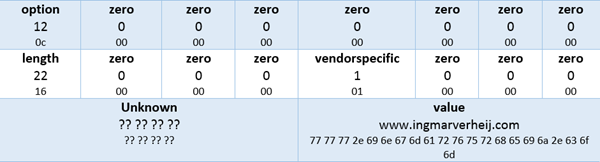
Each DHCP option the following structure is used:
- The first byte contains the option code, followed by 7 zeroed bytes;
- Next is a byte containing the length of the value, followed by 3 zeroed bytes;
- Then a byte specifying if this is a vendor specific option yes (1) or no (0), followed by 3 zeroed bytes;
- Four bytes are filled with data I can’t explain, but it always ends with 0x51.
- Finally the value is stored (in Hex values) in a block size dividable by 4 (!)
Here’s an example of how a vendor specific option (DHCP option 43) with code 12 containing the data www.ingmarverheij.com is stored:
Data types
To present the data, as done with the PowerShell script, you must know the data type. Unfortunately this is not stored in the DhcpInterfaceOptions key, so that’s the reason I added the CSV files. For now I included the following data type: ip / string / time / dhcpmsgtype.
If the data type is not specified in the CSV file the data is displayed in Hex values (just like Wireshark, DHCP test client and the Windows registry).
If you receive a Dhcp option that’s displayed in Hex values you can change the CSV files or e-mail me a Wireshark capture of your DHCPOFFER.
.

Thank you!
I had been threatening to do this in ThinKiosk for ages and never spent time on it. This will save me alof of effort.
Glad I could help you developing ThinKiosk. If you have any questions, you know where to find me.
Good pro article! I’ve an issue with Nokia Lumia and Windows 8 option 55: both OS use the same!
Do you know how to alter (registry key, for example) this option ?
Many thanks
Roberto
Hi Roberto,
Each vendor (Nokia / Microsoft) has its own vendor class, based on this identifier you can send specific DHCP options to either your Nokia Lumia or Windows 8 endpoints.
More information can be found here:
http://www.ingmarverheij.com/microsoft-vendor-specific-dhcp-options-explained-and-demystified/
Ingmar
This is an awesome powershell script!
Ingmar – I’m having issues with this is I am connected to a VPN (Cisco to be specific) as it is only running on the “Gigabit Network Connection” Any Ideas?
For those needing help running it for the first time and unfamiliar with powerscript. In command prompt launch “powershell.exe .\ReadDhcpOptions.ps1”
Since this isn’t digitally signed you may have to change the powerscript setting to allow unsigned powerscripts.
powershell.exe Set-ExecutionPolicy Unrestricted
http://technet.microsoft.com/en-us/library/ee176961.aspx
Hi Wyatt,
Good tip on the ExecutionPolicy. It’s a parameter unknown by most people yet very powerfull.
What issue are you having with the VPN? Do you want to query the VPN connection as well? I’m limiting the output to Ethernet adapters but can expand it to more if you want?
Cheers,
Ingmar
Ingmar,
I would like to query the VPN Connection as well. I tried doing it by changing the powerscript shell but was unable to get it working. Perhaps if you can have the powerscript query the list of adapters and you could choose an interface adapter under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces
dhcptest is now on github.
https://github.com/CyberShadow/dhcptest
whats neat about the tool, is you could use it to get unsupported scope options on windows- ie option12
get you mac address via gwmi into $mac
then
$hostname = dhcptest-0.3.exe –mac $macaddress –request 12 –query –print-only –quiet
woops hit send too quick.
s/$mac/$macaddress
also need to put path .\dhcptest-0.3.exe
Thanks for this script, it works great.
Above you stated it would be possible to expand the script to include VPN connections. I have an issue that needs that functionality. I am trying to pass option 252 for proxy PAC assignments. I am using Cisco AnyConnect VPN and code I have on the ASA states this is possible, but I haven’t been able to get it to function. I am unsure if the option is getting to the client and something else isn’t working correctly.
I am very new to PowerShell and wouldn’t know where to start to try to add it myself.
Any help would be appreciated.
Ryan
Thank you very much for the script. It is very helpful. There seems to be a small bug in the script though. Line 102 should read:
$DhcpIsVendorSpecific = $DhcpVendorSpecificOptions[$intPosition]
Great script, but unfortunately it does not read all options offered by DHCP, e.g.option 66/67 (PXE boot server/file) are not listed. I don’t think it’s related to the script though (as it cycles through all 256 options)
Hi Ingmar, helpful powershell script you’ve provided here. Is there any way to see other DHCP info? For example, I’ve specified Option 42 (NTP) and Option 66 in my DHCP scope, but they aren’t showing up in the Powershell script results nor in the DHCP test client results.
Thanks to author!!!
Really usefull! The only article through the internet!
Just about tail 0x51. It’s diffs from system to system.
Great script, thanks!
Minor error, the location of the exit statement inside of foreach ($objNACItem in $objWin32NAC) block will terminate after the first adapter. Moving the exit statement outside of that block allows the script to iterate over all of the qualifying adapters.
And Option 3, Router, should be an ip type in the csv.
This will only partially answer the issue, however, since RFC 4702 says it can have a series of IPs. The length should be a multiple of four. You would get the first router in the list, though.
As the csv stands now, it outputs ASCII representations of the IP octets.